D-Link DIR-600 is a cheap home router, currently unsupported in
USA/Canada, but supported and widely used in Latin America.
In February 2011, I sent vulnerability information about command execution on D-Link DIR-600 to D-Link Chile, then to D-Link Latin America but after sending many e-mails I haven't got any response.
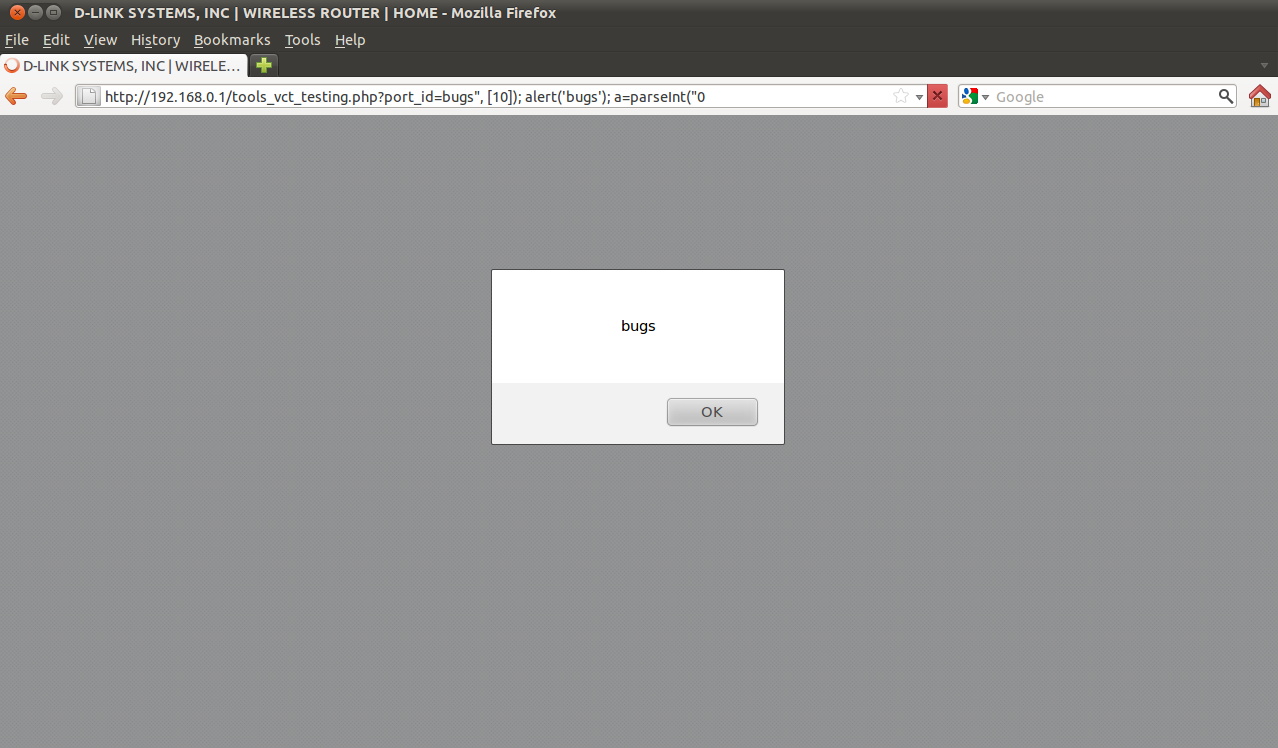
Cross Site Scripting (XSS)
A common XSS was found in DIR-600 web interface.
http://router_ip/tools_vct_testing.php?port_id=bugs%22,%20[10]);%20alert('bugs');%20a=parseInt(%220
Command Execution
It's a video about the vulnerability and its exploitation.
Currently, all firmware versions are vulnerable (2.05, 2.0). This vulnerability requires administrator privileges, but the default firmware version (2.0) is vulnerable to HNAP flaw too, discovered by SourceSec Security Research. A combination of these two vulnerabilities turns out a remote code execution exploit without the need of valid authentication credentials.
I expect that D-Link contact me to patch responsibly the vulnerability and to provide an updated firmware version to users. I will disclose soon technical details about this vulnerability and the research I've done (telnet access, fun
with busybox and so on).