Update 1: Movistar, a day after this post was published, contacted me to solve the security problems.
In this article I'll show two vulnerabilities found in the router FiberHome HG-110, provided by Movistar in large numbers to its clients in the last time. I must clarify I'm currently a client of Movistar Banda Ancha Hogar and I have the prior mentioned router, being the purpose of this research to inform its clients and Movistar pays attention in answer to these vulnerabilities.

Firstly, this report begins with a briefly analysis of known vulnerabilities so far. Then I describe in general terms the discovered vulnerabilities and the videos of the exploits in execution, to demonstrate the severity of the vulnerabilities and neither the vulnerable page nor exploit code I'm going to make public at this moment. The third part are the workarounds that the clients can put in practice to avoid being victims of attacks exploiting these vulnerabilities. In the end, I present a study about Movistar network, the number of routers FiberHome HG-110 and the security implication that these vulnerabilities have, with the timeline of responsible report of them.
Prior vulnerabilities
Zerial, in April 2011, disclosed Local File Include and Cross Site Scripting vulnerabilities in the router FiberHome HG-110. Then in August, MSH Inc published a further review of issues with text plain files and remote scenarios. Other web pages like MiNuevoHogar or Taringa have posts with information about router credentials and how to configure the router.
Discovered vulnerabilities
The discovered vulnerabilities represent a higher degree of severity than currently known ones. Next I show the videos of exploits in execution, but I'm not describing details that could lead to vulnerability discovery. It's necessary to clarify two things about the videos:
- The remote host, that exploits the vulnerabilities in the router, is located in an external network (Internet) and not inside the local network.
- The vulnerabilities affect services at ports 80, 443 and 8000. These last two are commonly opened towards Internet.
Remote access to SSH as root
Remote command injection
Workarounds for the vulnerabilities
Since the vulnerabilities are in the services available through the ports 80, 443 and 8000, the router must reject the access to them from an external host. The configuration of the router is a bit complicated to set up firewall rules, though through SSH and iptables it gets easier. The quick solution showed here it's not ideal but it works.
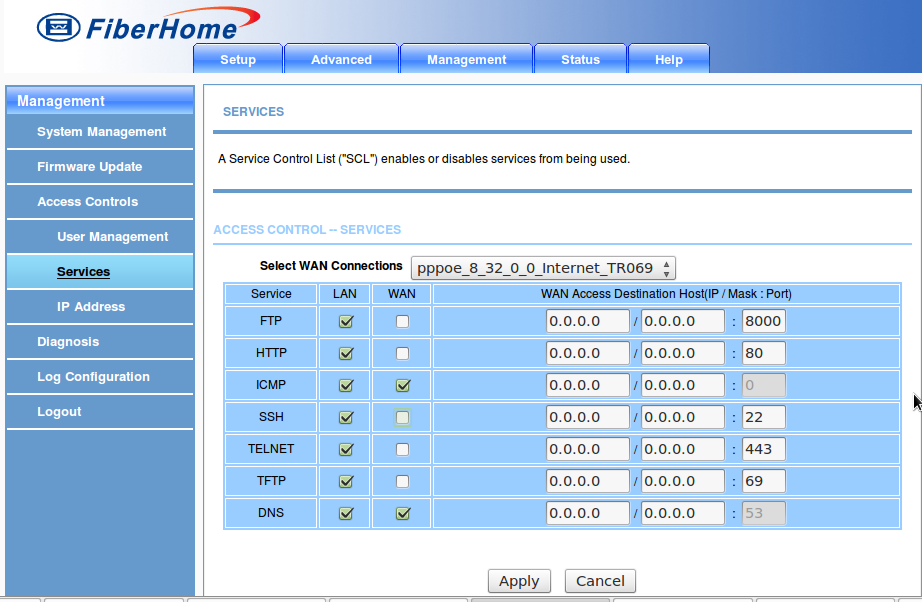
The router has management control over the services it offers. The administration interface is at the port 8000 and you must go to the section "Management / Access Controls / Services". What I did was to configure the FTP service at the port 8000 and Telnet service at the port 443, and allow access only from inside the LAN. I chose those services because I don't use
them. A screenshot shows the final situation.
Implications for Movistar
The router FiberHome HG-110 is currently being installed by Movistar. In the case an old modem fails or clients require more bandwidth, they will encourage you to accept this new router. Here I present a little study about the participation of this router in the network of Movistar Chile and I conclude with some conclusions about it.
The size of the sample was 68974 hosts that replied successfully the following queries:
- Ping
- Port scanning at ports 22, 80, 443, 8000
- NETBios Query
This sample was obtained a Sunday day in the afternoon, during a lapse of three to four hours to avoid the router repetition in the sample due to connection/disconnection. Subsequently the sample was analyzed through search of patterns in the router responses, giving the following results:
- In the NETBIOS query, 13859 hosts replied with the string
HOME\BAMOVISTARWIFI@BAMOVISTARWIFI [00-00-00-00-00-00], which is a sign that it's the router FiberHome HG-110. This means that currently over 20% of the clients had the router and the trend points out this number will grow up on the time. - 13204 hosts of the prior 13859 hosts had the router with ports 443 and 8000 opened. It corresponds to more than 95% of the clients.
The routers FiberHome HG-110 come with a daemon that often checks for new firmware updates. Today, with the latest firmware, 19% of the hosts of Movistar network would be vulnerable to the vulnerabilities here described. Although the remote access as root couldn't be successful, the command injection vulnerability will be in most cases.
The vulnerabilities here described can favor the implantation of sniffers in client routers. There are a large number of attacks that an attacker can do, since all the data have to go through the router. Ideas like a botnet can be feasible as there are thousands of vulnerable routers.
Regarding with the notification of these security problems, in January 2012 I tried to contact Movistar through its helpdesk. An employee replied me he couldn't pass the problem up the chain, so he suggested me to go to an office. In February 2012 I sent an e-mail to FiberHome, the router vendor, which one wasn't answered. As in both cases, the probability of answer is
low or none, I made public this information.
Conclusions
It's worrying to me, as Movistar client as security researcher, the severity of the discovered vulnerabilities. This router is currently being distributed in other countries like Colombia and Argentina, so the vulnerable clients grow up in an exponential way. I expect that Movistar contact me to resolve this security problems in a responsible way and they give a patch for their clients.